
stardom dreams, stalking devices and the secret conglomerate selling both
"this is all so stupid," maia keeps repeating
content warnings:
abuse/controlling behavior, murder/homicide, stalking
people frequently reach out to me with companies to look into. usually it takes me about 10 minutes before i move on for one reason or another—it's not interesting for a story or has good security, for example. i didnt expect anything different when an acquaintance told me about Tracki, a self-proclaimed "world leader in GPS tracking" that they suspected could be used nefariously.
at first glance, Tracki appeared to be a serious company, maybe even one that cared about security. we could never have guessed what was about to unfold before us.
half a year into our investigation, we'd found it all: a hidden conglomerate posing as five independent companies, masked from governments and customers alike through the use of dozens of false identities, US letterbox companies, and an undeclared owner. a 90s phone sex scheme that, through targeting by one of hollywood's most notorious fixers, spiraled into a collection of almost a hundred domains advertising everything from online dating to sore throat remedies. a slew of device-assisted murder cases, on top of potential data breaches affecting almost 12 million users, ranging from federal government officials to literal infants. and most importantly, a little-known Snoop Dogg song. how in the world did we get here?
starting our descent
Tracki's website is littered with stock illustrations of gps pins and reviews praising it for its reliability and customer service. they tout their popularity on sites like amazon, comparing their seemingly superior specs and prices to those of similar gps trackers. but a bit of googling will have you run into blog posts on their site discussing stalkerware (as well as how to get rid of it) and explicitly marketing Tracki as a device for spying on a spouse or other family member, even providing detailed instructions for attaching it to their car. and with further prodding, it's also quite easy to make the connection from Tracki to its parent company, Trackimo (registered in israel as VESTIGO TECHNOLOGIES LTD), with Tracki being their more consumer-focused brand and Trackimo, who does the actual product development, focusing on business applications. despite this connection, however, Trackimo chief operating officer Amit Shaked confirmed to us that Tracki operates largely independently of Trackimo. having sent a local contact to check, we are able to confirm that Vestigo has an office space located in central tel aviv, housing most of their in-house R&D, management and software development employees.

Trackimo also has some pretty big business partners, with Vodafone Business selling a whitelabelled version of Trackimo's devices and app, Leica Geosystems providing a gps tracking and remote control technology co-developed by Trackimo, and many other big telecommunications companies officially reselling their devices. additionally, in collaboration with Beta (an israeli VC incubator formed by Paramount), they co-own a subsidiary called watchinU that offers a Nickelodeon-branded smart watch for kids, the "NickWatch". while currently only available in the UK and israel, it features gps tracking for parental monitoring, two-way chats and calls with parents or other contacts, a photo-taking and editing app, preloaded music, various games, a step counter, and some other applications encouraging physical activity. given the steep cost of the device at almost $180 USD, not including the monthly data plan required to use it, we decided against getting one for testing (even though i really want to play around with it).
Tracki devices, however, are relatively cheap, usually costing around $60 USD but sometimes dropping down to as low as around $10 USD, which i was far more willing to spend. the package was dispatched from a warehousing company in new jersey and UPS (surprisingly enough) delivered it within a week.

setting the device up was fairly easy. the mobile app lets you scan a QR code inside the battery compartment to pair the device with your account. upon connecting the device, the app prompts you to subscribe, with the cheapest option costing $20 USD per month. besides their mobile app, Tracki also provides a web interface with all the same features. both interfaces prominently feature a map showing where all your trackers are located, differentiating between the more accurate gps location and less accurate approximate location based on cellular tower and wifi information. they also provide access to the more advanced features of the trackers, such as geofencing alerts, setting up the SOS button, movement alerts, and a crucial feature for stalking use: disabling all noises the device makes, like low-battery beeps, with a single settings toggle.
information security is, as always, lacking
while i was playing around with the web interface, the .git exposure-checking browser extension i use alerted me that, as is cliché in these articles, Tracki was leaking the git repository for their interface. a cursory look through didn't reveal anything particularly interesting, but it gave me confidence that there were probably similarly egregious security holes elsewhere, so to get a basic idea of the attack surface i grabbed a list of subdomains and started going through them.
most of the subdomains were customer-facing sites or simply returned error messages, with the occasional internal tools in between. one of those tools particularly caught my attention: on the surface, the completely blue login page simply entitled "TRM" may seem boring, but a look at it using dev tools reveals a complex client-side rendered react frontend. and after a second or so of load time, the debugger tab in dev tools showed me the full original source code and directory structure. and... oh my god, they're shipping with source maps! using sourcemapper i downloaded a local copy as well, to make working with it a lot easier.
after some quick searches, i identified various hardcoded usernames and passwords used to load data from a number of administration and support tools, including their inventory management software, support chat tool, zammad helpdesk, and console for their sim card and mobile network provider. yet another set of admin credentials for that helpdesk were also found hardcoded in their mobile app (inside the built in bug report/support request feature), an issue which—alongside others—had already been reported to Tracki all the way back in 2021 but was never completely fixed.
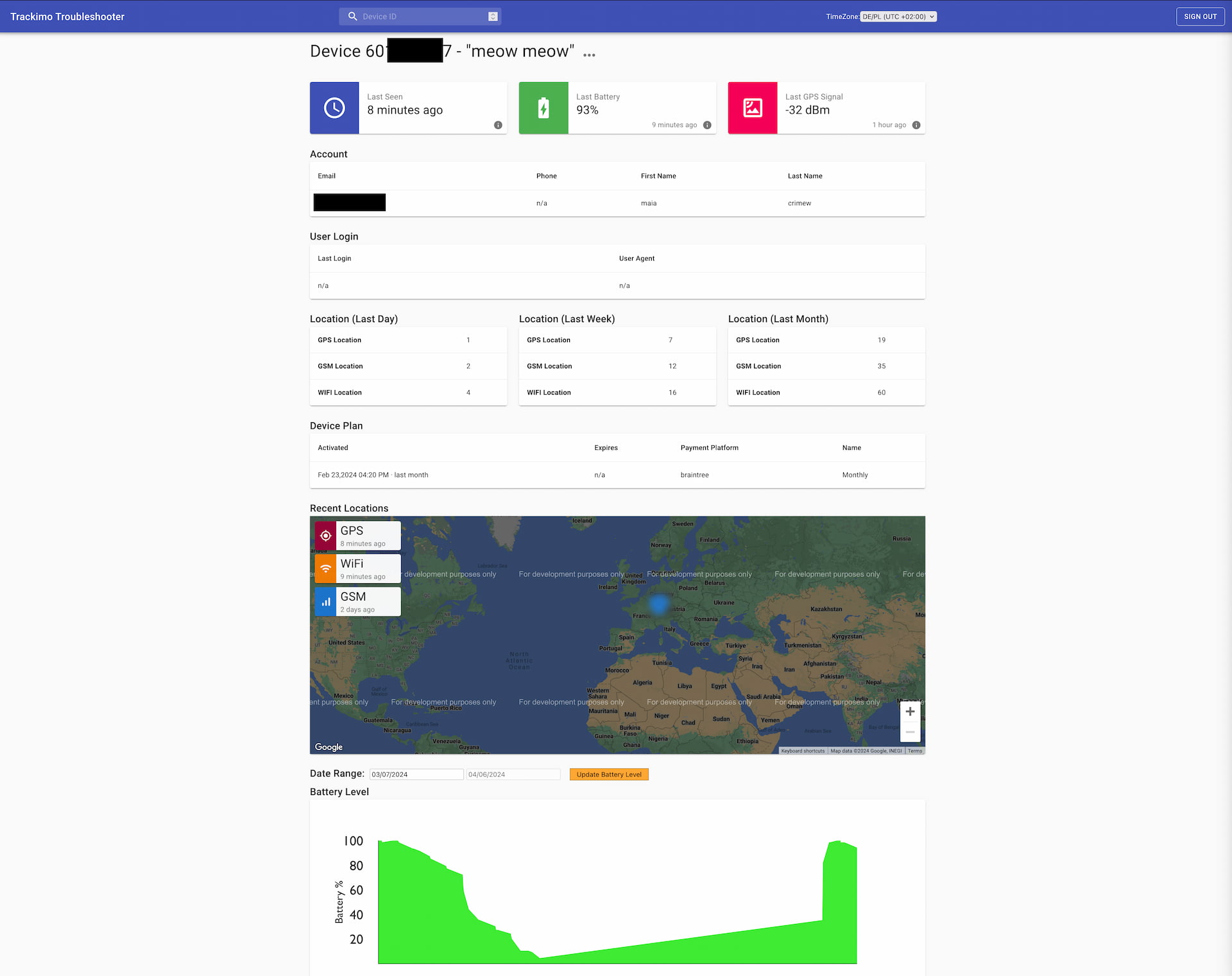
from the list of subdomains i also found another interesting support tool, the "Trackimo Troubleshooter". based on the frontend source code and some educated guesses, i assumed that this tool would be used for remote debugging of all Tracki and Trackimo devices, showing technical support agents practically all the data from any given device by just entering a device id.
the tool itself seemed fairly solid, with no blatant vulnerabilities, but since it's a simple internal support tool, it doesn't have a user account system. instead, authentication works by logging in with a single shared password, and all it took for me to find said password was digging up an email in the helpdesk introducing the tool's features to various Tracki and Trackimo employees and informing them of the password. given that the tool requires no input besides a device id (which all follow a standardized format), it would most likely be possible for someone to grab all sensitive device and subscriber information for most (or all) devices. lmao
a city in the philippines
the helpdesk is also interesting for the amount of company information it reveals. most employee names seem american, and Tracki is legally registered in delaware, but internal email addresses instead call back to the philippines. connected linkedin profiles show the company is indeed based in the central filipino city of cebu.
described in a bloomberg column as "the most typical place in the world", cebu has the quintessential characteristics of any city the US would build a military base next to: a bustling tech sector, rich suburban and urban regions, and a high density of low-cost labor. one of the most impressive subdivisions is cebu's IT park, a grid of palm tree-lined highways and roundabouts that connect an array of highrises and their surrounding buildings.

on the 17th floor of skyrise 4, you can find the offices Tracki operates from. upon a local contact going there, however, we actually found a shared office space rented in part by UniversalTech (or 'UTech'), a filipino outsourcing company with no legal nor public affiliation with Tracki.
internally, however, Tracki acts purely as a dummy corporation, helping hide UTech and its employees from the public eye. Tracki CEO Mikhael Cook, along with other executives, holds the same role in UTech, and payrolls are disbursed through UTech instead of Tracki; in fact, Tracki legally has zero salaried employees. product owner Andrew McMennamy spearheads the front, with the support lead—Tom Dillon, at the time of our initial research, though he no longer works for the company—acting as a de facto legal department despite their lack of formal legal experience.
We technically have an address [in New York] for legal and/or tax reasons, but as far as I know there's no Tracki personnel anywhere inside the USA. Tom Dillon, responding to a police inquiry
and the support lead's role is quite important: Tracki is provably very popular among stalkers. support receives multiple subpoenas per week from local and federal law enforcement worldwide, frequently for stalking or harassment but also occasionally for other charges, including domestic violence, attempted murder, and murder, all of which involve the victim being tracked down using a Tracki device. the company is not only aware of these uses, but has even actively assisted customers in nonconsensual tracking of individuals via their helpdesk.
in one case (not involving assistance from Tracki personnel), a perpetrator attached a Tracki device to the car of an ex-partner in order to discover her new residence, where she lived with a new partner; the perpetrator then fatally stabbed the new partner more than 80 times. in another case, a Trackimo device was used for drug trafficking in the lead-up to a violent triple-murder, including the execution-style shooting of a 6-year-old. at least two other cases also carry a murder charge, but their investigations remain in progress.
of course, there are other uses. both ICE and CBP frequently find gps trackers on vehicles crossing the united states border, leading to the agencies subpoenaing Tracki, presumably to trace potentially illegal cross-border movements. on the other hand, adjacent agencies and military programs in the united states, on top of other governments around the world, also use Tracki devices, typically for asset, personnel, and vehicle tracking.
at least they're making bank
elsewhere in the company, things operate with only the occasional hitch. Tracki makes most profits via ecommerce, including sales in regional marketplaces, sometimes managed via UTech accounts. their monthly gross revenue falls at around $1.5 million USD, according to an internal income statement obtained from their helpdesk.
other bank statements also obtained from their helpdesk show that a significant portion of this revenue is then wired to Trackimo, their aforementioned parent company, and Wintrack (registered in hong kong as WENXUN TECHNOLOGY CO, LTD), a shenzhen-based contractor they work with. the values of these deposits across three months are shown below:
| november 2023 | december 2023 | january 2024 | |
|---|---|---|---|
| trackimo (israel) | $850,000 | $710,000 | $818,000 |
| trackimo (US) | $550,000 | ||
| wintrack | $250,000 | $495,000 | $430,000 |
an accountant knowledgeable in US finance tells us that these movements indicate that Tracki is simply a "mediary to move cash through", having no stock and poor financial health. the small profit it does make per year isn't enough to bring it out of the red, and not much cash is left in company-owned accounts, holding around $99 thousand USD by the end of the year despite their estimated $19 million USD in revenue.
a smaller portion of the overall funds is also wired to two individuals: the aforementioned Andrew McMennamy and israeli-american businessman Amiram "Ami" Shafrir. over three months, the accounts paid differ:
| november 2023 | december 2023 | january 2024 | |
|---|---|---|---|
| mcmennamy | $5,000 | $5,000 | $15,000 |
| shafrir | $50,000 | $75,000 | $62,500 |
these direct payments tend to be unusual for corporations, and not only because they are off payroll and seemingly not a result of contractor work, but also for the amount of money in each payment. other employees at UTech are paid an average of about ₱250,000 ($4,400 USD) per year, a mid-range salary for the filipino support industry. McMennamy, for one, tops that in a single month.
and Shafrir is even worse, sometimes being paid more in a month than even McMennamy seems to make in a year. but who is he? a keyword search for his name along with "tracki" on google provides no results, nor with "trackimo", nor with "universaltech" or "utech". but a second search on the helpdesk brings up old emails from him, signed:
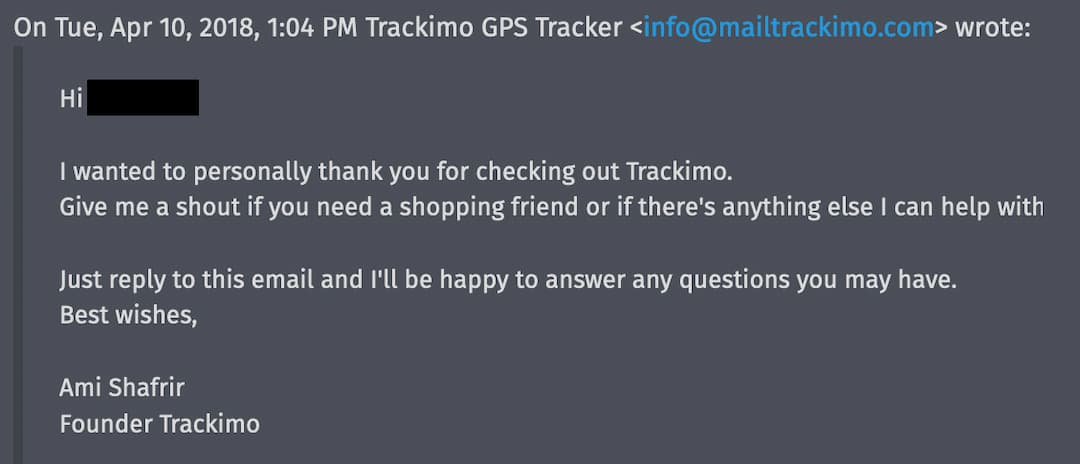
founder? of Trackimo? the other three founders—Shai Bar-Lavi, Amit Shaked and Shlomo Shur—are extremely public about their roles, and Shafrir's seemingly never been mentioned anywhere. and elsewhere on the internet, he seems like he's had many other large positions: CTO of IBM (archive)? marketing manager at zone & co (archive)? really, who is this guy?
the ami story
Ami Shafrir has had a, well, complex relationship with the business world. in 1992, he founded his first and most successful business, amtec audiotext, which—in the words of haaretz editors—is "a technical name for a sex-calls operation". in its best year, 1995, Shafrir claims it generated $60 million USD, and it continued to be wildly profitable. his internet company, worldsite, became the center of the rest of his business operations in the tech sphere.
that was until until 2000. two years prior, Shafrir's wife had filed for divorce and soon after befriended Daniel Nicherie, who claimed he was an investment consultant and lawyer. in reality, however, he was a career fraudster, and as the divorce got ugly in 1999, he used the trust he'd built to defraud the pair out of at least $40 million USD. by the end of his scheme, Nicherie had taken ownership of Shafrir's companies, hit him with more than 100 lawsuits, hired a notorious private investigator to wiretap him and seized everything from his office to his home.
i never went after innocent people. never. Anthony Pellicano, the private investigator hired to wiretap Shafrir (source)
following Nicherie's eventual 2004 indictment, Shafrir got back on his feet and started pursuing a new venture: online talent auditions. by 2006, he was affiliated with upwards of 75 domains covering auditions for everything from film to modelling to theater. the domain that prevailed and remains up today is ExploreTalent.com, with some other domains (like Auditions.com) persisting as sub-brands. Shafrir continues to be its co-owner.

so as the 2010s progressed, how did he find his way into the gps tracking business, an industry he'd never touched before? a search for ExploreTalent on the Tracki helpdesk shows that the connection between the two may be more tangible than is obvious: support periodically sent emails from an ExploreTalent domain, and internal management spreadsheets show that UTech support employees had their roles divvied up between the two companies.
a deeper search further brings up a linkedin description (archive) from ExploreTalent's former CTO, who describes UTech as "an exclusive [IT outsourcing] company to support www.ExploreTalent.com and its satellite online properties". and remember TRM, Tracki's custom-built support tool that contained hardcoded credentials? its source code, in fact, also contains numerous references to ExploreTalent's backend, presumably as a stopgap while ExploreTalent didn't have their own support tool.
this leaves the companies less separate than expected: if Tracki is essentially UTech, but UTech is actually meant to exclusively serve ExploreTalent, then the three must be at the very least close. and what's the connection between gps tracking and talent auditions, anyway? what's the big deal with ExploreTalent in the first place?
hollywood hates this one simple scam and basically you're stupid
in their marketing, ExploreTalent promises stardom to aspiring actors, models, and musicians. representatives lure in these individuals with promises that attract both those experienced in the industry and those looking for a start, including landing roles at disney or in other films with well-known stars. the only thing representatives say you have to do is subscribe to their "PRO" membership, costing $290 USD per year. and with all that big talk it makes sense that many think that ExploreTalent is a talent agency who's about to help them make their big break in hollywood.
in reality, however, ExploreTalent is nothing more than a talent listing service—instead of having a dedicated agent vying to get you roles in the entertainment industry, it makes people create profiles so casting directors can mass-review users on the site for their unfilled roles, or let the talents audition to posted casting calls. the caveat is that barely any of the "big guys" in hollywood actually use these services, so at best some ExploreTalent users get cast for a number of small independent films while paying obscene amounts of money, hoping for that big break.
this is no small distinction—the claim has seriously tricked a great number of people. on the united states' better business bureau, ExploreTalent is given the lowest possible rating by user reviews. one rather succinct comment reads, "Fake job leads 0% job leads Fake profiles posing as legit people", followed by a censored 12-letter expletive. others report being tricked by campaigns intended to get people to buy their nearly-$300 USD "PRO" membership, which has elsewhere been described as a "scam" and "misleading".
ExploreTalent.com and your boy Bigg Snoop Dogg! we been hooked up mane, so log on right now if you wanna see what time it is, if you wanna get in contact with somebody [jumpcut] like myself, Bigg Snoop Dogg Snoop Dogg, on whether ExploreTalent is a scam (archive)
it is of note, however, that some of those user reviews may also be based on misinformation relating to ExploreTalent. some theories focus on the fact that Ami Shafrir is israel-born and jewish as well as his former role as founder of amtec audiotext, the aforementioned phone sex company. posts promoting the theories make ExploreTalent out to be some sort of large-scale sex trafficking operation, with all the expected anti-jewish vitriol sewn in to boot. others instead focus on the fact that the site used to host talent profiles for significant republican figures like Candace Owens and Lauren Boebert, alleging that the site was somehow directly involved in their rise to the jobs they hold today. but that's doubtful, especially because of the site's clear difficulty with getting its users their wanted roles; the much more reasonable explanation is that the to-be pundits and politicians were, like many others in their field, simply failing actors or models before their move into politics.
we have graphql at home
having already found various smaller vulnerabilities in the ExploreTalent website, i didn't expect much in terms of security from them. i'd already seen the basic format of their backend requests from Tracki's TRM, so simple guessing of common endpoints almost immediately resulted in me finding their complete api documentation :3
most of the documented endpoints returned very little or no useful info without authentication, but as soon as i signed up for a basic talent account and grabbed my authentication header, a lot of them started working, spewing out the personal information of all 11.4 million registered users on the site. and it appears i wasn't the first one to discover this either: names, emails, passwords, phone numbers and home addresses of around 5.8 million ExploreTalent users were leaked onto a hacking forum all the way back in february 2022, though the breach was not reported on by any news outlets. thanks to the OSINT data platform intelx having archived a copy of the data leak, though, we were able to confirm the authenticity of the 2022 data.
but ExploreTalent's backend is even more vulnerable and ignores even more best practices than the 2022 hacker realized. the api, for example, has sql injection built in as an internally used feature, allowing a client to add to any database query made by the backend and extract even more data or arbitrarily filter its result. the interface documentation also implies that one of the endpoints i had access to used to return user passwords in plain text, which explains how the hacker was able to obtain this data in 2022. this assumption is further corroborated by an internal ExploreTalent sales training video displaying a support tool, which shows that user passwords weren't just stored in plain text—already atrocious security practice—but also actively displayed to ExploreTalent employees.
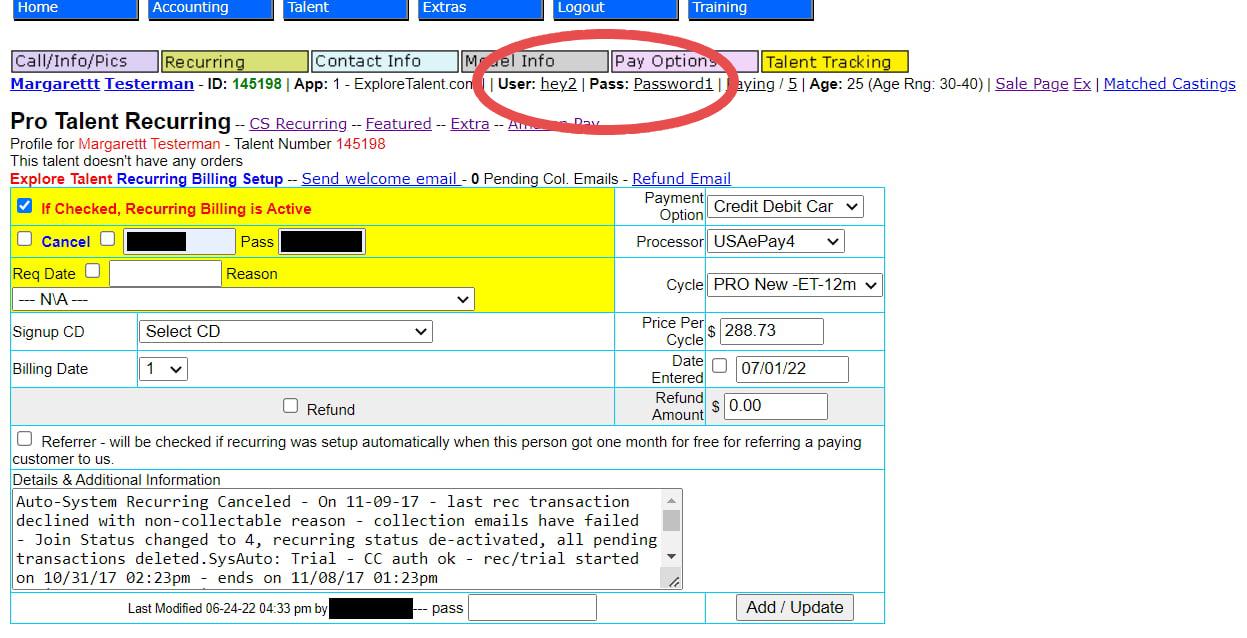
i used the newfound ability to run arbitrary database queries to search for my test user profile based on my password, which promptly succeeded. so even though the api won't just spit out passwords anymore (no matter how hard i tried to convince it using custom queries), it would still allow a malicious actor to match usernames, emails and all other user data to collections of popular or dictionary-generated passwords, resulting in password lists that can be used for credential stuffing on other services.
the fact that they fixed the plaintext password exposure post-breach (albeit without improving how they were stored internally) indicates that ExploreTalent most likely noticed when they got hacked back in 2022. but even as its existence became known to some users via breach notification services, ExploreTalent still failed to inform their users of the incident, going out of their way to lie about its existence in assuring customers that "there is no truth to the claim that Explore Talent has exposed your personal information to hackers". they also allege that dark-web breach monitoring services—including the US government-affiliated MyIDCare—rely on "bait tactics" to sell paid subscriptions, adding that ExploreTalent "take[s] pride in maintaining the utmost security and safeguarding our users' data" by "adher[ing] to stringent security measures and industry best practices to ensure the protection of user information".
and finally, crypto tiktok
pretty early on into the research of this article, we found ourselves looking at other companies connected to higher-ups at the mini-conglomerate we'd found thus far. Mikhael Cook and Andrew McMennamy, two of the most authoritative figures at Tracki, had an odd connection: they were CEO and CMO of another company, lit.it, which offers a cryptocurrency shortform video app. for some reason, we initially discarded it as another vaguely connected but unimportant venture. even though we found emails in the Tracki helpdesk clearly meant for Ami Shafrir but instead sent to an "Ami" working at lit.it, we assumed they were completely different individuals because the surnames didn't match—this lit.it CEO had the name Ami Berg instead of Shafrir. it was only when we decided to revisit this lead way later (primarily because at this point maia had been making constant jokes about "crypto tiktok" on our work calls) that Berg's linkedin profile (archive) started seeming more and more suspect. the bio and past positions seemed oddly similar to Shafrir's, with small details differing between the two; the oddly arrogant and braggy tone in the bio felt eerily familiar, and even the profile picture just... kinda looks like Shafrir back in the 90s or early 2000s.
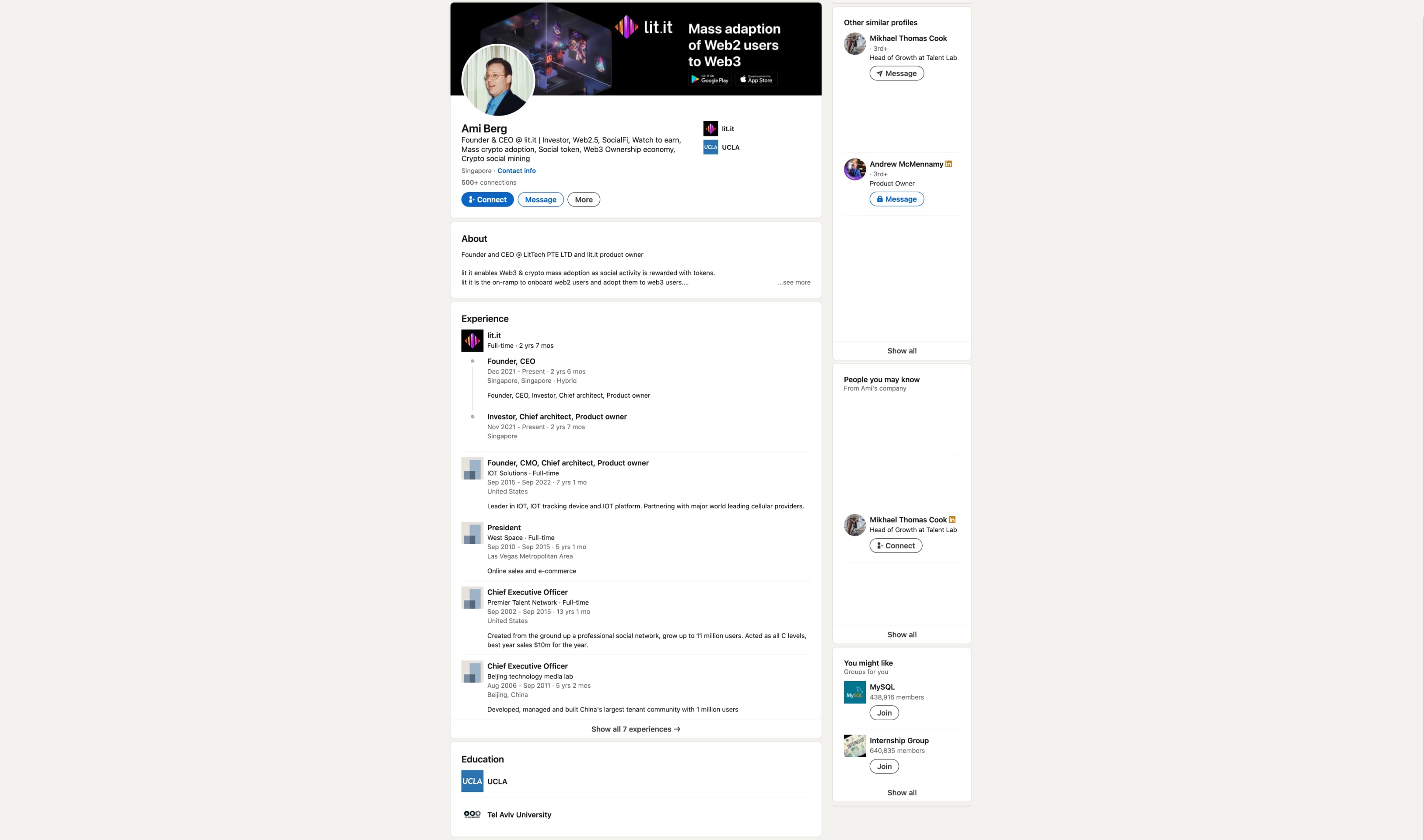
while neither Premier Talent Network nor IOT Solutions exist under those names, those descriptions sure do match ExploreTalent and Trackimo! and things just didn't seem to line up—Berg could be found nowhere on the internet outside of this linkedin page, and his account (the username of which ends in "-lit") was created around the launch of the app. furthermore, upon contacting the UCLA registrar's office, officials confirmed that no student named "Ami(ram) Berg" (nor "Ami(ram) Shafrir", for that matter) ever graduated from the university. the page appeared entirely falsified.
this all seems like an attempt by Shafrir to assume an alias in order to redeem his public image, a practice he previously called out when his archnemesis Daniel Nicherie did the same. and this isn't even the first time Shafrir has attempted to make it harder to find out about his past: sometime in late 2021 (about a year before the Ami Berg linkedin profile was created), he commissioned someone to spam the internet with as much positive information about him as possible. this campaign included the creation of spammy profiles on every public social media-adjacent website imaginable, paid articles on spam blogs, badly put-together slide decks on powerpoint sharing websites, medium blog posts, and youtube videos. the content published includes complete lies about Shafrir's past, partially caused by the spammer mixing him up with Amit Shafrir, a completely unrelated israeli-american tech businessman. a lot of the spam also includes various photos of ami hanging out with celebrities (mostly as a part of his work at ExploreTalent), where we once again see the spammer getting a little bit confused.
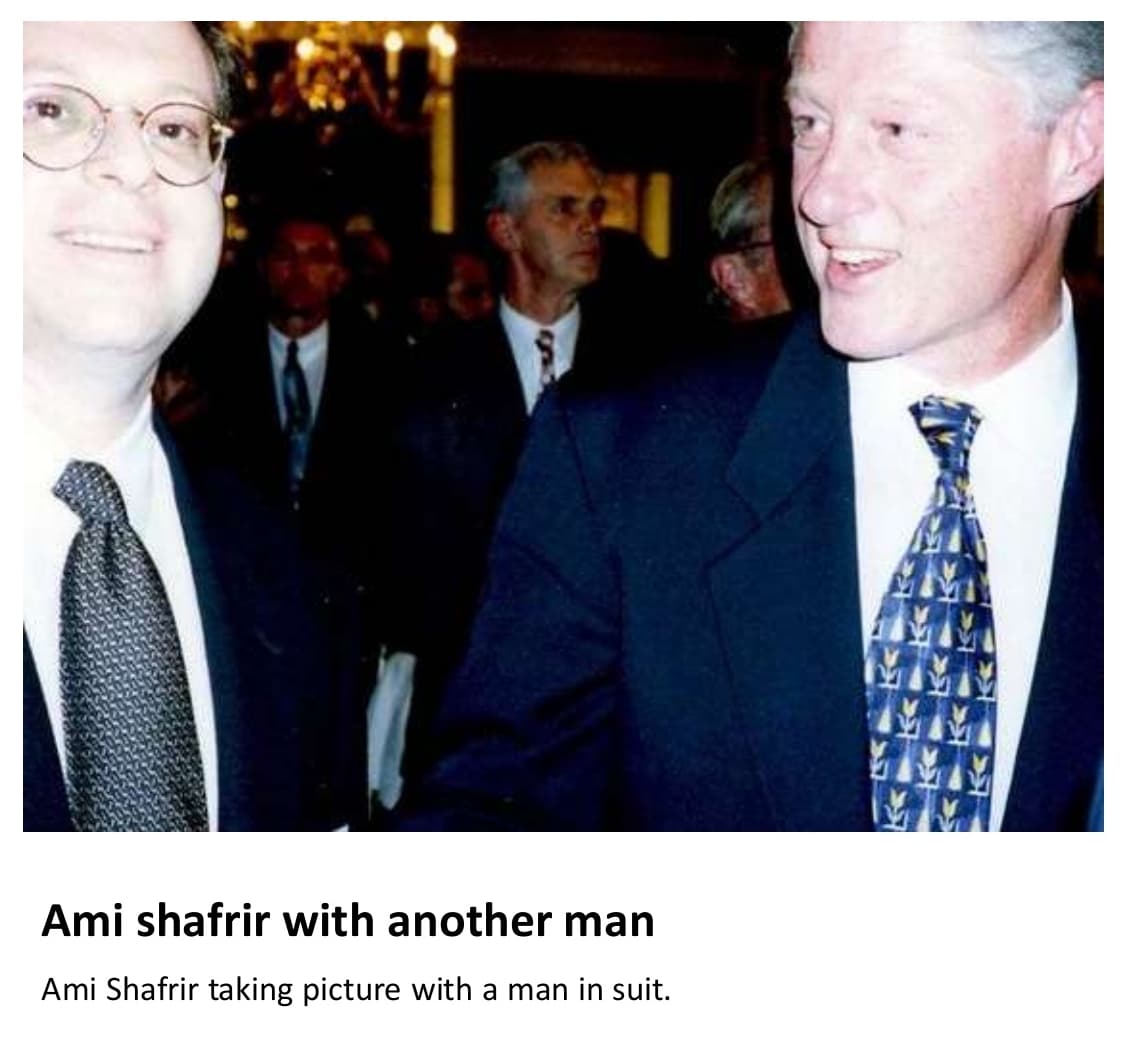
shafrir's lemonade stand
"I would not trust Ami Shafrir to run a lemonade stand, let alone a company handling millions of people's sensitive data", Cooper Quintin, senior staff technologist at the Electronic Frontier Foundation, told us. the security flaws in both Tracki and ExploreTalent indicate to him that the companies put a "priority on making as much money as fast as possible and do not give one moment of thought to anything that stands in the way of this goal, such as basic security measures."
all security vulnerabilities mentioned in this article were reported to Tracki and ExploreTalent prior to publishing. Tracki patched most vulnerabilities nearly immediately, and a significant amount of ExploreTalent's infrastructure changed shortly before publishing (thereby patching some others mentioned in this piece before we were able to even report them).
"We are committed to addressing any of the issues you brought", an email from the Tracki support team wrote. they expressed appreciation for the report, though they discarded implied connections to ExploreTalent as "old code sitting there" from an "old developer" who "kept it there from his prior project."
we further reached out to dozens of both current and former employees and executives within the companies for direct comment, but received no response from any. Quintin made the danger of these security lapses in Tracki and Trackimo's services clear. "This is one of the most horrifying examples of stalking technology I have ever seen", he wrote. "Trackimo should be investigated by the FTC and shut down immediately for their complicity in so many horrendous crimes."
Update 08/22/2024: a sentence was added to clarify the relationship between Tracki and Trackimo, based on information provided to us by Amit Shaked (COO of Trackimo)